
Business
How we got here, and where we are headed
Mike Malone
April 28, 2022
Visit Smallstep at booth #2045 during RSAC 2026!

Business
Mike Malone
April 28, 2022

Business, SSH
Mike Malone
April 13, 2020

Business
Mike Malone
February 28, 2020

Technical
Mike Malone
September 24, 2019

SSH, Step Certificates, Technical
Mike Malone
September 11, 2019
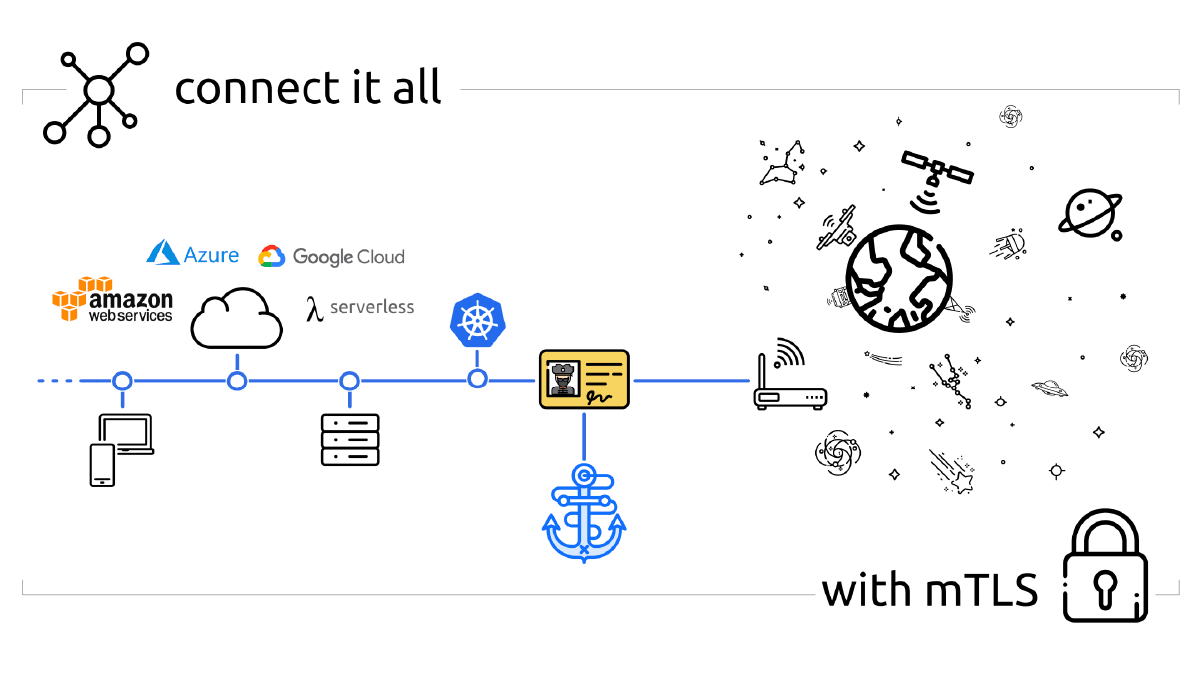
Step Certificates, Technical
Mike Malone
May 2, 2019

Step Certificates, Technical
Mike Malone
December 11, 2018

Step Certificates, Technical
Mike Malone
December 11, 2018

Business
Mike Malone
November 20, 2018

Business, CLI
Mike Malone
August 7, 2018