How to Bring Your Own Root from AD CS to Smallstep

Linda Ikechukwu
In a previous article, I discussed why organizations should consider migrating away their legacy PKI from Microsoft's Active Directory Certificate Services (ADCS) to a modern, consolidated, and robust platform like Smallstep.
Although not yet officially sunsetted by Microsoft, Active Directory (AD) is not well aligned with Microsoft's strategic prioritisation of their Azure cloud services. Microsoft has been encouraging customers to replace AD with their cloud-based "Entra" identity services. However, Entra does not include certificate services, which means many enterprises will have to continue relying on legacy AD CS deployments to support essential Enterprise IT functions like WiFi and VPN. This wouldn’t be an issue if AD CS was still actively developed. In fact, the last “What’s New” update for AD CS was in 2016, meaning that the cost of supporting AD CS keeps increasing over time as the rest of the ecosystem evolves in incompatible ways.
Smallstep offers support for all legacy enrolment protocols and validation services supported by AD CS, including SCEP, NDES, OCSP, and CRL. We also integrate directly with device management platforms like Jamf and Intune to register and enroll devices, as well as automate certificate management for WiFi, VPN, and browser clients. These features allow for a smooth transition from your legacy AD CS.
Furthermore, with our Bring Your Own Root (BYOR) feature, you can deploy Smallstep in parallel with your AD CS deployment and start using it within minutes, without any risk. To get started, you just need to upload your existing AD CS root CA certificate to the Smallstep platform. You’ll use the same root certificate to sign a Smallstep intermediate CA, which can be used to issue leaf certificates to existing or new subscribers within your PKI.
This tutorial will guide you through the process of importing your root CA certificate to Smallstep and signing an intermediate CA that will be used to issue certificates on your behalf.
Step 1: Export your Root CA certificate from your AD CS server
To Bring Your Own Root to Smallstep, you need to upload your AD CS root CA certificate to Smallstep. To do that, you’ll need to export the root CA certificate from your AD CS server in PEM format (P.S: Do not export or upload your root private key to Smallstep). Here’s how to do that:
- On your Windows server interface, type in ‘mmc’ into the search bar and hit Enter to open the Microsoft Management Console interface.
- Go to File > Add/Remove Snap-in.
- In the Add or Remove Snap-ins window, select Certificates, and then click Add.
- Choose My user account and then click Finish.
- Click OK to save the snap-in settings.
- On the resulting Console screen, click Certificates (Local Computer) > Trusted Root Certification Authorities > Certificates.
- Select and right click your AD CS root certificate, and then select All Tasks > Export from the drop-down menu.
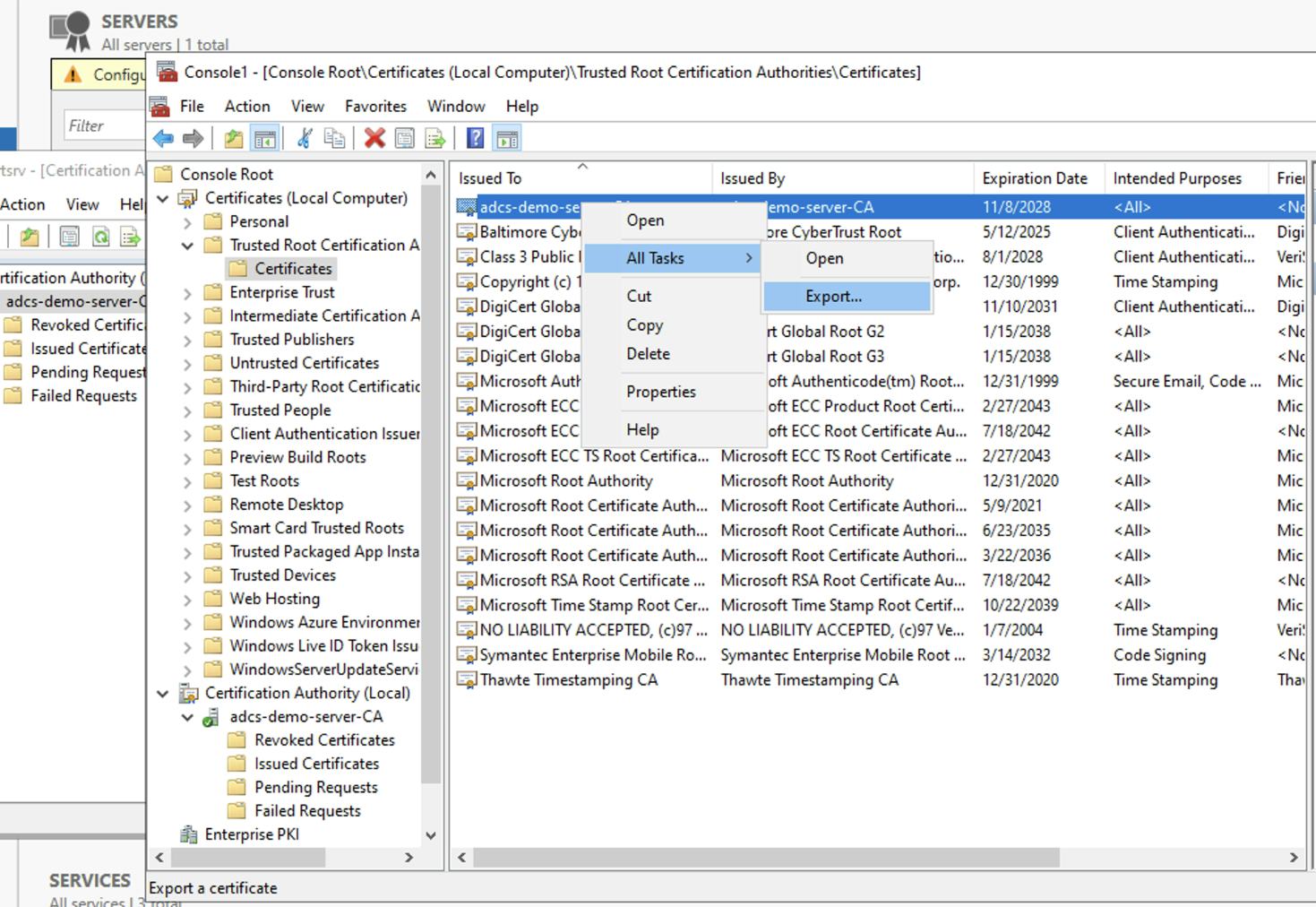
- In the Certificate Export Wizard, click Next.
- In Export File Format, select Base-64 encoded X.509 (.CER), and then click Next. Smallstep requires you to upload a PEM file. PEM files are are Base64 encoded, so that works.
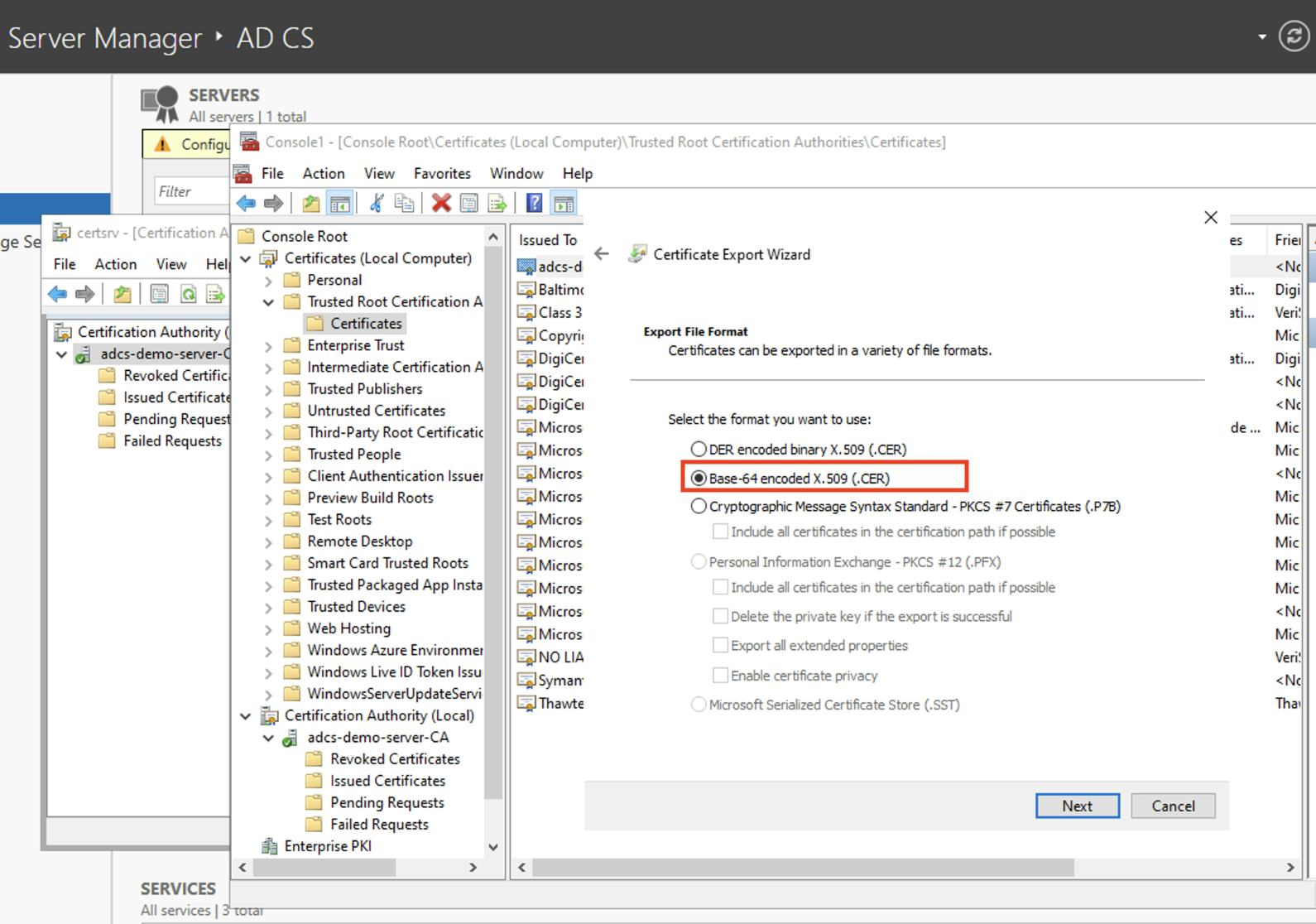
- Select a location where you want to export the certificate, provide the name of the certificate file, and then click Next > Finish.
- Copy the CA certificate file into your local machine for where you can upload it to Smallstep. You will need it for the next step.
Step 2: Set up a new Authority on the Smallstep Platform
Now that you’ve successfully exported your AD CS root CA certificate, you can now upload it to the Smallstep platform to create a new intermediate CA. Here’s how to do that:
- Create a Smallstep Certificate Manager team account if you haven’t already.
- Sign into your Smallstep team.
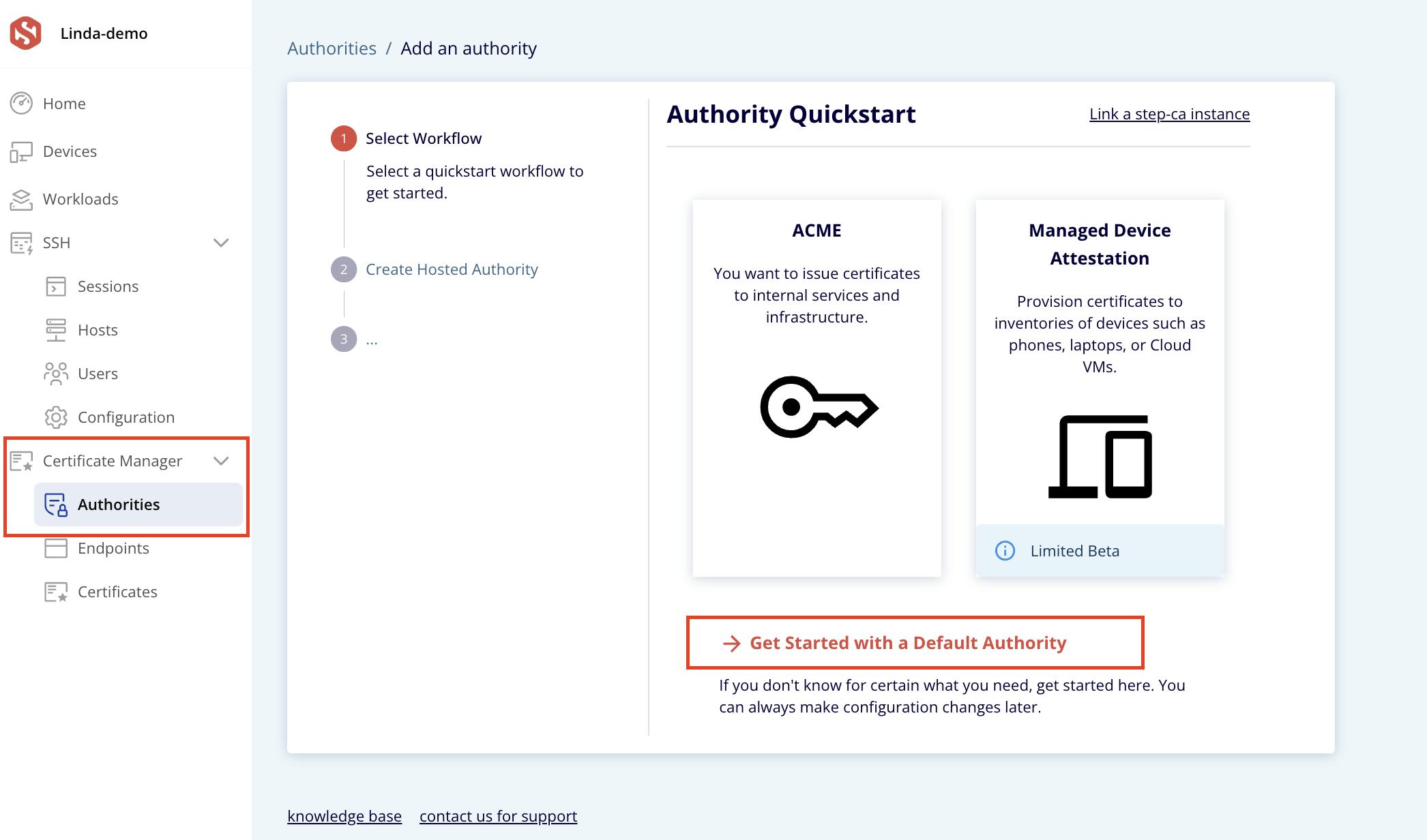
- Go to Certificate Manager > Authorities in the main menu.
- Click Add an Authority.
- Select the Default Authority workflow.
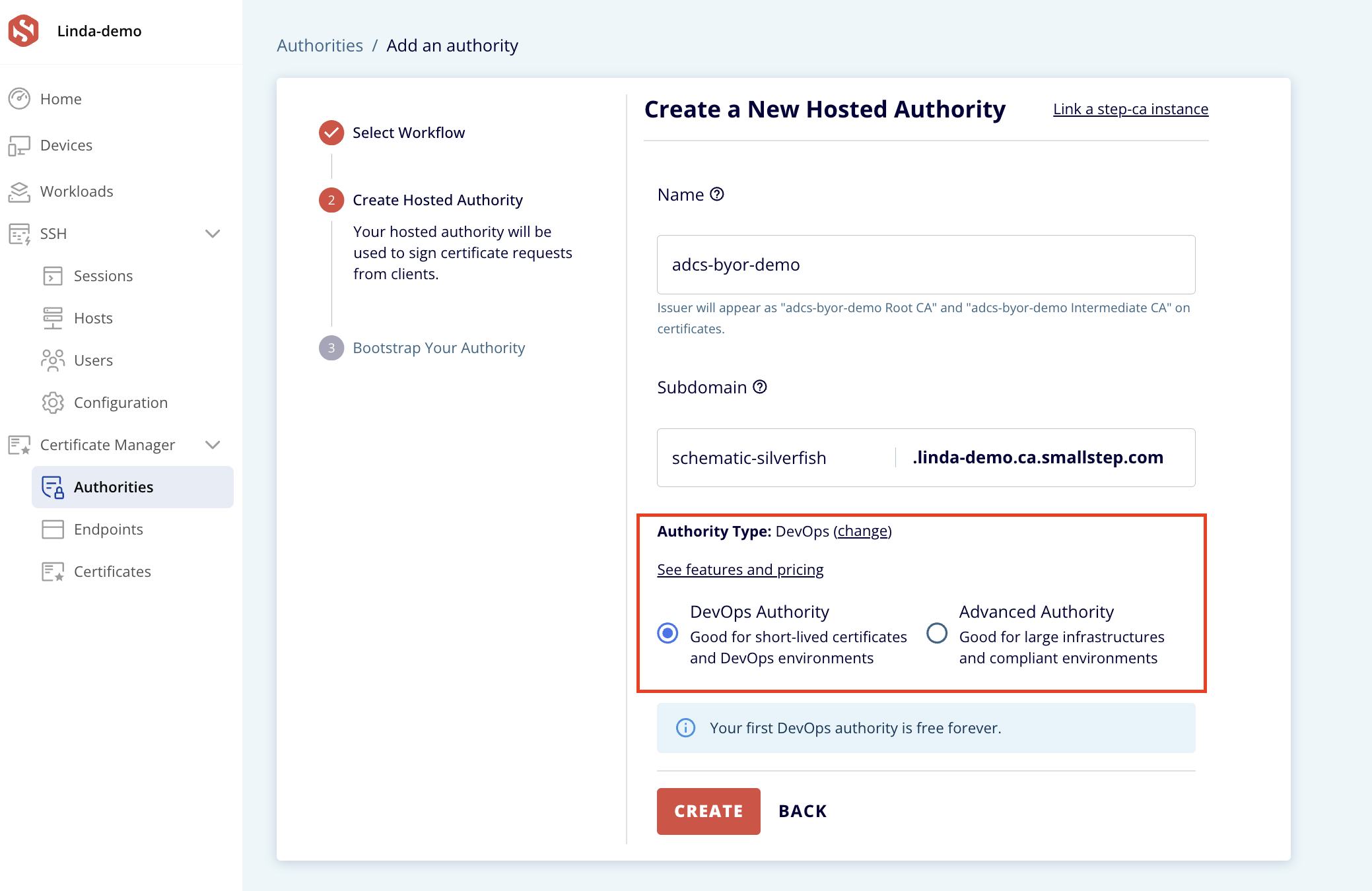
- Give your new CA a name and subdomain, and change the Authority Type to Advanced Authority. Then click Create. (The BYOR feature is only available on advanced authorities).
- On the next page, select "Upload external root." Now, upload your AD CS root CA certificate which you exported and copied to your local device in the previous step. Click Next.
- Specify a Common Name and Signing Key Type for your Intermediate CA. Click Create CSR.
- A CSR will be generated. You’ll need to download and sign this generated CSR using your offline root.
- Click Download CSR Certificate.
Step 3: Sign downloaded CSR with offline AD CS root key
The final step in bringing your own AD CS root into Smallstep is to sign the generated CSR with your offline AD CS CA private key. Please do not export your private key for any reason. Your root CA certificate which you uploaded in the previous step will be used to verify that the signed CSR.
- Copy the resulting CSR file from your local machine into your Windows Server machine, where you’ll sign it with your offline AD CS root key.
- On your Command prompt, run the command:
Replace csr-9e63a172-EXAMPLE-5b0c7.csr with your own generated CSR file name.
- (Optional): If you see that your request is “pending”, this means it has gone into AD CS’s approval queue. You will need to approve it before you continue. To do that, open the AD CS Server Manager, open Pending Requests, find your request ID, and select Issue.
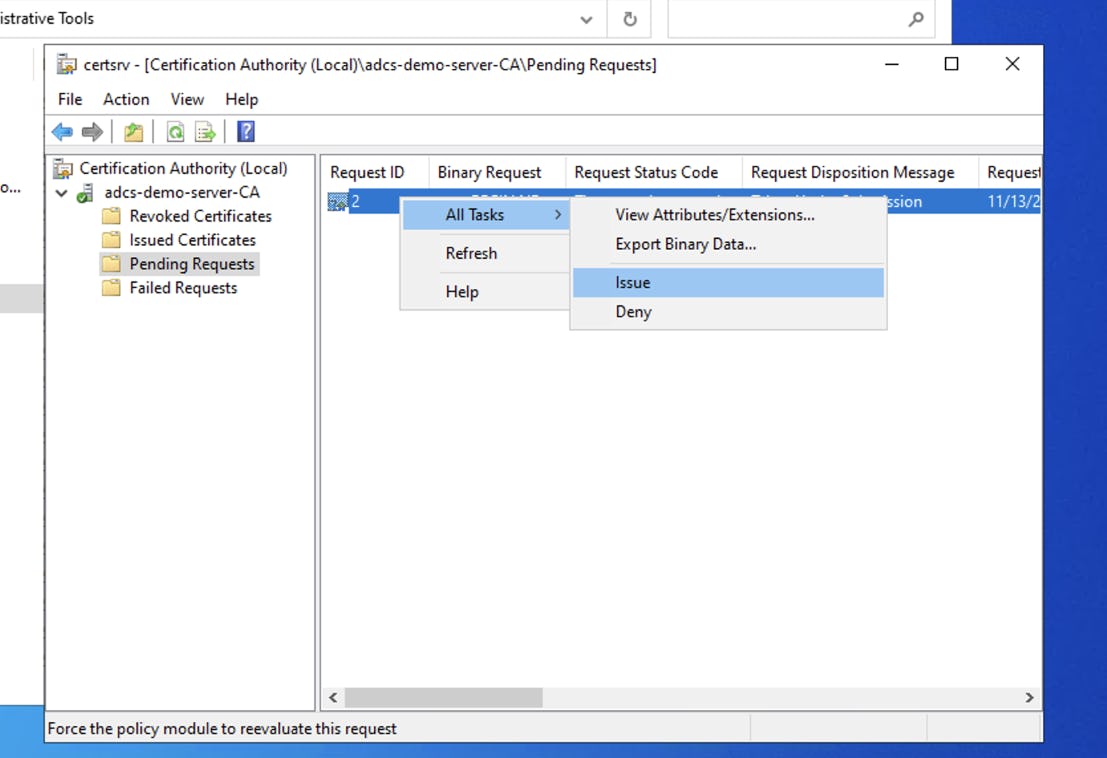
- Once you’ve approved it, return to Terminal and run
certreq -retrieve 2 intermediate.crtto retrieve your new Intermediate CA certificate. Replace 2 with your request ID. - Finally, upload your Intermediate CA certificate to Smallstep, and we'll create your new CA.
Conclusion
Congratulations you’ve successfully brought your own AD CS root into Smallstep. You’ve taken the first step to migrate away from your legacy AD CS PKI. All of your clients that trust your existing root CA will now trust your Smallstep CA as well. You can continue to use your existing CA infrastructure to issue certificates as needed, then slowly make plans to migrate away from it completely.
Smallstep’s BYOR feature allows you to migrate from your legacy PKI at your own pace, while introducing better security (the use of intermediate CAs means that you can you can easily rotate your intermediate signing keys without much fuss, since they aren't generally included in trust stores) and automation (using ACME) to your infrastructure.
Linda is a wannabe guitarist, who reads African literature or fiddles with a tennis racket to unwind while navigating the daily grind of helping growth-stage tech startups drive adoption and awareness of their products through tailored content strategies that translate concepts from arcane technical domains into plain and accessible language.



