Certificate Based Wifi Authentication With RADIUS and EAP-TLS

Linda Ikechukwu
Mathematics is more trustworthy than people or software. Therefore, when designing a system, prefer security that is enforced by cryptography instead of software or personnel policy. ~ 1password
Certificate-based wifi authentication uses digital certificates to establish the identity of a user or device on a wifi network. It provides a higher level of security compared to more common wifi authentication methods such as WPA2-PSK or WPA2-Enterprise (such as EAP-PEAP and EAP-MSCHAPv2) that rely on passwords or shared credentials.
Here at Smallstep, we believe that certificates should be used for authentication whenever possible, and for good reason. Certificates are resistant to the data breach attack vectors that passwords and shared credentials are susceptible to, such as phishing, brute force attacks, dictionary attacks, and credential spraying.
If you have never heard of certificate-based wifi authentication or if you have but do not know much about it, you have come to the right place. This article covers what EAP-TLS and certificate-based wifi authentication are, how they work, the benefits they provide, and what your organization stands to gain if they are adopted.
In the beginning was 802.1x
We can’t talk about enterprise wifi authentication without doing a little refresh on the 802.1x standard. Let’s time travel for a bit.
Before 2001, the most common method for connecting users to workplace networks was via shared passwords or MAC address filtering. However, the shared credential approach proved challenging to scale as workforces grew, and also led to data breaches due to inadequate identification and access control. Enterprises cried out for better ways to identify and authorize access to their networks.
In response to this need, the Institute of Electrical and Electronics Engineers (IEEE) developed the IEEE 802.1x standard. 802.1x provided a framework for centralized configuration, management, and regulation of access to both wired and wireless Local Area Networks (LANs), as well as the services and applications running on these networks. Instead of using a shared credential for all clients, access credentials can now be set up individually for each client.
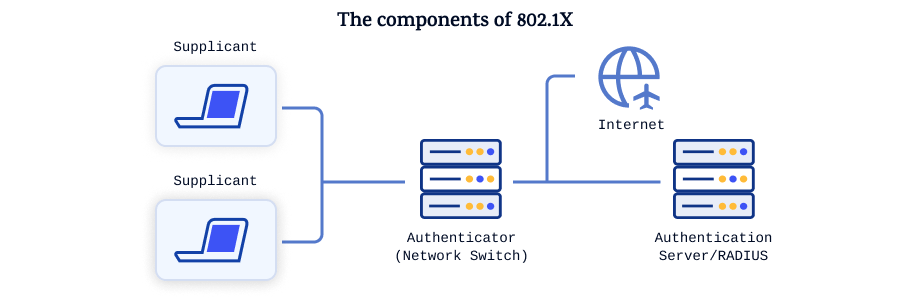
The 802.1x standard defines four basic functional components for centralized network access management. These are:
- The applicant/supplicant: a client computer in a LAN or WLAN attempting to connect to the network. Since the terms "applicant" or "supplicant" can be confusing, I will use the term "client" to refer to them for the remainder of this article.
- The negotiator/authenticator: for example, a LAN switch or WLAN access point or switch
- The authentication server: for example, a RADIUS server or LDAP gateway
- A user directory: for example Active Directory or a database
When a client needs access to a LAN or WLAN, it first contacts and sends its credentials to the negotiator (such as a switch or WLAN access point). The negotiator accepts the request and forwards the credentials to the authentication server (such as a separate RADIUS server). The authentication server then consults the user directory to verify that the provided credentials belong to an authorized user eligible to access the network. Based on the verification of the credentials, the authentication server either allows or denies logical or physical access to the local network.
802.1x with EAP-TLS
EAP which stands for Extensible Authentication Protocol, is an extensible authentication protocol for network access developed by IETF [RFC3748]. It is used in situations where the Internet Protocol (IP) is not available and provides secure methods for sending identifying information over-the-air for network authentication.A rite of passage that everyone who tries to grasp 802.1x must go through is being confused about how EAP and 802.1x relate to each other. That’s totally understandable. I had to bang my head against the wall and munch on several packs of popcorn before I finally got it.
So here’s the deal: EAP, as an authentication protocol, was originally designed for use within the Point to Point (PPP) protocol, which is used to directly connect one device to another. The Point to Point protocol initially specified two authentication mechanisms: Password Authentication Protocol (PAP) and Challenge Handshake Authentication Protocol (CHAP). However, people wanted more authentication options, so the EAP protocol was introduced.
EAP sat inside PPP’s authentication protocol to provide support for authentication mechanisms beyond the original PAP and CHAP protocols. These mechanisms include the usage of Kerberos, certificates, and public key authentication, as well as hardware schemes such as authentication dongles, smart cards, and USB tokens.
When the 802.1x standard was being designed, the IETF didn’t want to reinvent the wheel for the authentication part of the standard, so they borrowed the EAP framework from PPP. Therefore, you can say that the 802.1x standard adopted the already existing EAP for authentication instead of defining its own authentication mechanisms. The 802.1x standard defines how to pass EAP packets over LANs (EAPoL) for authentication between the client, the access device, and the authentication server over a wired or wireless LAN.
So, while 802.1X defines how to control network access based on authentication, it relies on EAP to perform the actual authentication. You can say that 802.1X "uses" EAP to provide the authentication methods within the 802.1X framework. The client and authenticator use EAP to exchange messages. When a client sends a request to access the network, whether by plugging in a network cable or attempting to connect to a wireless network, the network switch or wireless access point to which the client is connecting responds with an EAP request, instructing the client to provide its credentials.
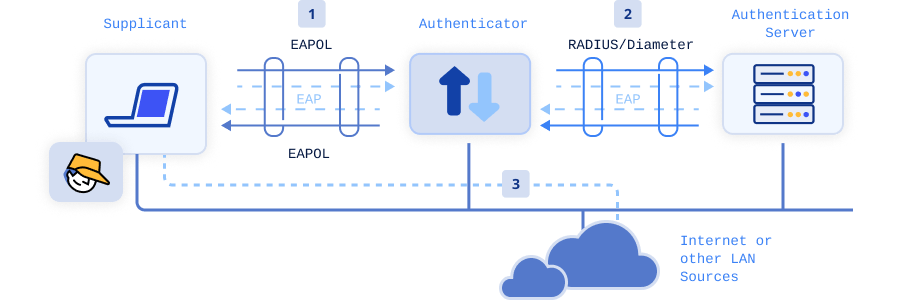
EAP specifies functions for different authentication credentials called EAP methods. These methods can use various credentials such as usernames and passwords, digital certificates, or biometric data. For wireless networks, the commonly used EAP methods include PEAP-MSCHAPv2, EAP-TTLS/PAP, and EAP-TLS. If your organization uses passwords for WPA2-Enterprise, you're likely using one of former methods. But we’re not going to discuss those. The most important method here is EAP-TLS.
EAP-TLS is regarded as the most secure authentication protocol for 802.1X networks, and uses certificates for wifi authentication.
How WPA2/WPA3-Enterprise Wifi certificate based authentication with EAP-TLS works
To implement EAP-TLS certificate based wifi authentication at scale for your organisation, you need additional components outside of the supplicant (client) and negotiator (wireless access point), namely:
- An internal PKI or certificate authority: Since EAP-TLS is certificate based authentication, you need a modern certificate authority platform like Smallstep to automate issuance and management of properly configured certificates to verifiable devices. Smallstep supports the modern ACME DA for device certificate enrollment as well as legacy enrollment protocols and validation services like SCEP, NDES, OCSP, and CRL. No matter what MDM you’re using, Smallstep will integrate nicely with it.
- MDM server: optional, but it really helps. A device management platform like Jamf, Intune, or SimpleMDM makes it easy to deploy certificates and configure wifi correctly without confusing end users. Smallstep supports SCEP and ACME DA for enrollment. SCEP is a legacy protocol, but it works everywhere. ACME DA [IETF draft] works on Apple, Windows, and Linux running up-to-date OS versions. It uses cryptographic device attestations for the highest assurance that only specific devices can join your network.
- RADIUS server: A Remote Application Dial In User Service (RADIUS) server is used to authenticate, authorize, and account for users attempting to connect to embedded routers, modem servers, software, and wireless apps. A RADIUS server determines whether a user can access a local or remote network and, if granted access, what privileges they have on that network. On an enterprise scale, a RADIUS server is highly beneficial. Instead of configuring numerous separate networking and infrastructure devices, RADIUS is a centralized mechanism for faster onboarding of new devices to wifi networks. The use of RADIUS server is what makes EAP-TLS Wifi authentication more secure because it allows for mutual authentication. The client device can authenticate the RADIUS server to ensure that it is authenticating to the right network, and avoid connecting to a spoofed network.
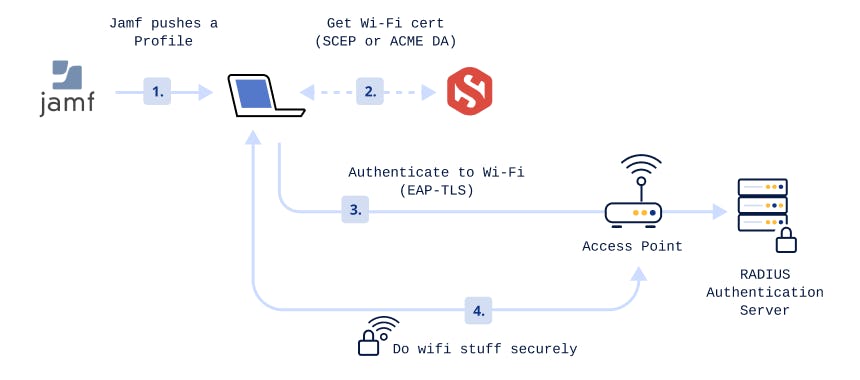
Regardless of the MDM solution you use, a certificate-based authentication flow with EAP-TLS for WPA2/WPA3-Enterprise wifi can be summarized as follows:
- The device enrolls with the MDM.
- The MDM installs the root CA certificate on the device and pushes a profile and a SCEP or ACME DA payload to the device, instructing it to request a client device certificate for wifi from the certificate authority, Smallstep.
- Smallstep verifies the request, generates a client certificate, and returns it to the device.
- The device contacts the RADIUS server through the Access Point to obtain it’s certificate and ensure it is authenticating to a trusted RADIUS server.
- The device verifies that the RADIUS server certificate is from a trusted root. It does not connect to a RADIUS server that it doesn't recognize. This is why EAP-TLS is considered the most secure wifi authentication method, as it protects users and organizations against attacks like Evil Twin, where an attacker creates a duplicate RADIUS server to harvest user credentials.
- The device then uses the generated client certificate to request access to the network via the Access Point, which forwards the request to the RADIUS server.
- The RADIUS server verifies the authenticity of the certificate by examining its digital signature and ensuring it was issued by an approved Certificate Authority (CA) and has not expired or been revoked.
- If the verification is successful, the RADIUS server sends an accept message to the Access Point, which grants the device wifi access. However, if the verification fails (e.g., due to the device not being authorized or not having the correct access policy), the RADIUS server sends a reject message to the Access Point, and access is denied.
This rigorous certificate validation and key exchange process ensures that only authenticated and authorized users on enrolled devices, which are secure and compliant with valid certificates, are granted access to the network. This substantially enhances the overall security of the network. From the user's point of view, the entire process is seamless.
Here's a video under 2 minutes that demonstrates how to set up EAP-TLS Wifi authentication in Jamf with Smallstep:
Benefits of Certificate based EAP TLS Wifi Authentication
Certificate-based EAP-TLS authentication is considered the gold standard for network authentication security in WPA2 and WPA3 Enterprise Wifi, compared to its password-based counterparts like EAP-TTLS/PAP and PEAP-MSCHAPv2, for good reason:
- Superior Security Over Shared Credentials Systems: Certificate-based authentication is superior to shared credentials for several reasons. Passwords are a hassle to remember, and "stolen credentials" are often a leading factor in successful network breaches. Certificates, on the other hand, are something you have, eliminating the need to memorize or regularly change complex passwords. Users simply connect to the network and the certificate is automatically authenticated. For certificates, the private keys are never shared, making certificate based authentication phishing resistant.
- Faster WIFI Authentication Times: Traditional EAP interaction involves 22 steps from initial association to authorization. With EAP-TLS, it's only 4. EAP-TLS significantly reduces the number of steps for successful authorization and association onto the network, both initially and during device roaming on Wifi. This improves roaming capability and decreases latency. For networks that handle a large number of devices, EAP-TLS performs better than directory integration for association and authorization onto the network. Fewer authentication steps also mean faster network authentication, resulting in a better user experience.
- Eliminates Password-Related Disconnects: Since EAP-TLS primarily deals with certificates, there are no downsides related to password change policies. With a proficient certificate authority, certificate management can be fully automatic and hassle-free for your enterprise.
- Curbs MITM Attacks with Mutual Authentication: Server certificate validation is crucial in the authentication process as it prevents common over-the-air attacks like Man-in-the-Middle (MITM) attacks. MITM attacks exploit unsecured or misconfigured wifi networks, often by spoofing an SSID. EAP-TLS eliminates this attack vector by having the client verify the connection to a trusted network before connecting.
- Offers Better Fine-Grained Access Control: EAP-TLS authentication, using digital certificates, enhances network visibility and access control. Certificates provide valuable context information, such as user types, device ownership, specifications, authorization history, user roles, and current situation. This information improves network security and administration.
Get Certificate based Wifi Authentication for your WPA2 or WPA3-Enterprise Network with Smallstep
EAP-TLS certificate-based authentication ensures that credential exfiltration or compromise, including phishing, is impossible. Trusted by companies like Google, Meta, and Apple, our certificate-based approach is both secure and reliable. It addresses network security and privileged access use cases that are difficult or impossible to manage with other methods. We also offer a seamless drop-in replacement for legacy technologies such as Active Directory Certificate Services (AD CS).
In addition to WiFi, certificates used on managed devices for network authentication (802.1x / EAP-TLS) can also be used for wired/LAN and VPN connections, along with a Network Access Control (NAC) service that supports the RADIUS or RadSec protocol. Smallstep now supports these use cases.
EAP-TLS is widely regarded as the most secure network authentication method. However, despite its recognized security, it is not widely implemented due to its complexity. This is why what we are doing is important. To make EAP-TLS easier to implement, we’ve built our integrated RADIUS server into the Smallstep platform.
Sign up or log in to set up EAP-TLS, or reach out to our sales team if you have unique needs.Linda is a wannabe guitarist, who reads African literature or fiddles with a tennis racket to unwind while navigating the daily grind of helping growth-stage tech startups drive adoption and awareness of their products through tailored content strategies that translate concepts from arcane technical domains into plain and accessible language.


