The best secrets are the ones we keep to ourselves (I); Why passwords and OTPs suck

Linda Ikechukwu
Aside: This article is part of a three-part series exploring how shared secrets enable social engineering attacks and how adopting authentication methods that eliminate shared secrets (such as passkeys, TLS certificates, and device attestation) decreases the probability of social engineering attacks by a large percentage or eliminates it completely.
If you get nothing else from reading this piece, I want you to go away with this: passwords are no longer a reliable method for authentication or granting infrastructure access. Even when augmented with multi-factor authentication (MFA) methods such as one-time-passcodes, password-based authentication remains extremely vulnerable because secrets are shared.
In recent months, major organizations have all had their infrastructure breached. And, with all these breaches, one thing has remained common: attackers were able to obtain credentials and bypass MFA by employing different social engineering tricks. These attacks are, of course, not a reflection of the skills or capacities of the engineers or employees at these organizations.
The truth is, as long as your authentication method involves secrets (in the form of passwords or 2FA credentials) that need to be transmitted to, or stored on a database or server somewhere, credentials can be intercepted and stolen by attackers. Therefore, it's time for us to rethink our authentication processes and consider eliminating the Achilles heel of shared secrets.
The problem with password authentication: “A secret shared is a secret no more”
Out of 1000 IT, DevOps, and Security professionals surveyed in Teleport’s 2021 State of Infrastructure Access and Security report, 70% reported that they still use passwords to grant infrastructure access. But, what’s wrong with passwords anyway? Well, let’s start from the basics.
Passwords are inherently weak
Yubico surveyed 2,507 global IT professionals and IT security leaders, and 59% reported that their organization relies on human memory to manage passwords. When we have to rely on our memory to manage passwords, we default to simple passwords that are easy to remember (hence, guess) or reuse passwords from already existing accounts. This behavioral pattern is what makes passwords easy to hack through automated techniques like credential spraying, dictionary attacks, and brute-force attacks.
Most organisations advise and even enforce that employees should create strong, unique passwords for each account. However, with the hundreds of accounts that we all have, this is incredibly challenging and only results in increased costs for password resets because employees end up forgetting their passwords more frequently. This is why password managers were built.
 Source: XKCD
Source: XKCD
Password managers introduce a single point of failure
If your organization uses a password manager, that’s great! Password managers are good and definitely add a layer of security to the authentication process. They lift the security burden of passwords from users and take care of generating and remembering random, strong, and unique credentials for each account. Yet there is one password it doesn’t create: the master password.
Employees are still responsible for coming up with the master password, so there are chances that the master password won’t be unique. This means that the master password is still vulnerable to automated guessing techniques such as credential spraying, dictionary, or brute-force attacks (because humans on their own are prone to using weak passwords or reusing passwords).
The difference now is, if your password manager’s master password is compromised, the attacker doesn’t just have access to one targeted account but every single one of your accounts. This was the case when hackers launched a credential-stuffing attack using email addresses and passwords obtained from third-party breaches against users of the popular LastPass password manager.

MFAs can be phished
Many organizations use one-time-passcode MFAs as an added layer of security on top of plain password authentication; if you’re one of those, you’re doing well and certainly do have a better security posture than those who use just passwords. MFAs stop automated cyberattacks in their tracks, but they’re still vulnerable.
Just like passwords, code-based MFAs are still secrets, in that it’s like, ‘I know it, you know it. If you can prove to me that you know it by sending it across, you’re in”. Now, in the process of sending these codes along, they can be intercepted and stolen through different man-in-the-middle attacks or SIM swap attacks.
If those methods do not suffice, code-based MFAs can be phished. Phishing attacks have been quite successful because they leverage the weakest link in every security posture: human nature. The human mind can easily be distracted or tricked. Even people who are security aware/ conscious can still be victims of phishing attacks.
A common scenario that has been used in several corporate data breaches is this: an attacker spoofs the IT support phone number or email address and reaches out to an unsuspecting employee in your organization about a routine upgrade fix that requires the employee to log in and update their password. The employee is redirected to a phishing site that is exactly similar to the identity authentication screen they’re used to. As they enter their passwords and 2FA into the phishing site, the attacker retrieves the credentials and uses them to log into the actual site.

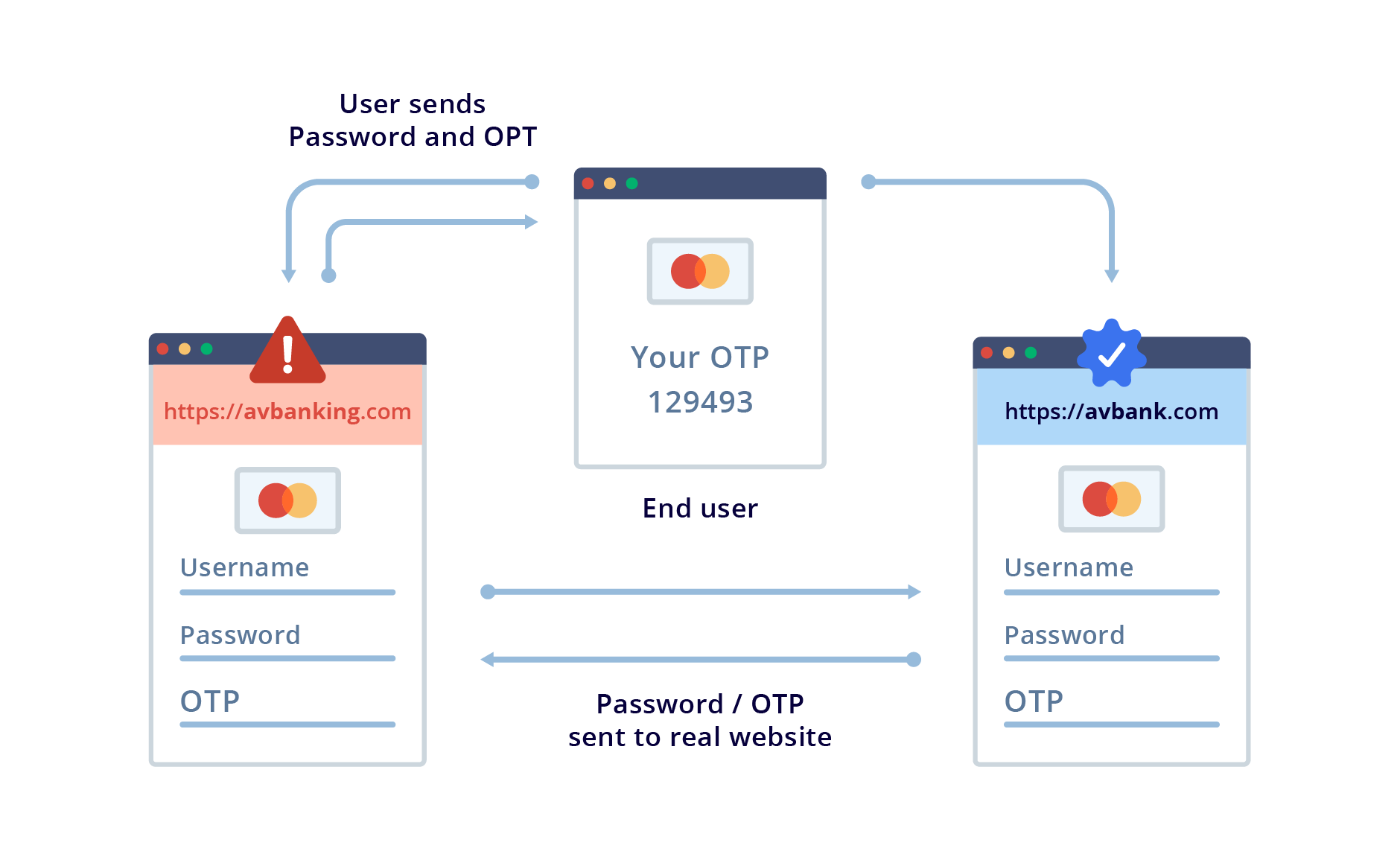
Still, on the topic of how easy it is to trick the human mind, even push-notification-based MFAs are now being overcome through a technique known as MFA exhaustion. In MFA exhaustion, an attacker in possession of compromised credentials repeatedly triggers push requests until the user caves and accepts the request in order to stop receiving the push notifications.
This technique was employed in the recent Uber hack. The attacker used an Uber contractor’s compromised VPN credentials to repeatedly attempt to log in, generating an MFA notification each time. The attacker even reached out to the contractor on WhatsApp, pretending to be with Uber IT support, encouraging them to accept. When they finally did, the attacker had access to the Uber VPN and tunnelled further into the Uber network to breach critical systems such as the company’s email, cloud storage, and code repository.

The solution? Keep your secrets to yourself; go passwordless
We’ve gone over the flaws of passwords + password managers + MFAs. I hope it’s clear by now that to stay ahead of the data breach and social engineering curve, we need authentication methods that incorporate the following capabilities:
- Does not make use of easy-to-guess credentials
- Does not put the burden of coming up with these credentials on the user
- Does not need to share or transmit sensitive credentials to prove identity
- Is not phishable (i.e cannot be tricked to handover credentials to an identical, but fake origin)
One method that satisfies all these requirements is using cryptography, specifically asymmetric cryptography. The next article in this series takes a look at alternate authentication methods that employ assymetric cryptography: PassKeys and TLS Certificates, discussing how they work to curb social engineering attacks, differences, and when to use which. Stay tuned !
About the author: Linda is an educator at heart, and her superpower is demystifying complexity. Since joining SmallStep as a developer advocate, her new mission is now to demystify and educate about PKI and digital certificates :)



