

We were building out new environments, and I didn't want to manage SSH Keys if I could help it.

SMALLSTEP SSH
Remove the need to gather, ship, and rotate SSH public keys for all your users and hosts. Smallstep delivers end-to-end SSH workflow that marries modern identity providers with short-lived SSH certificates and flexible access control. Available on-premise or as a managed offering.

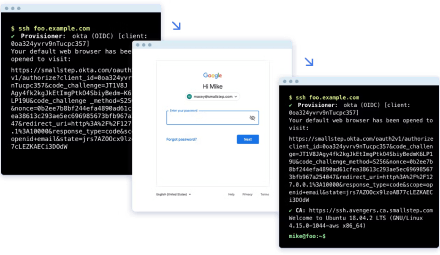
Users type ssh [host name] and are sent through your identity provider before connecting to the host.
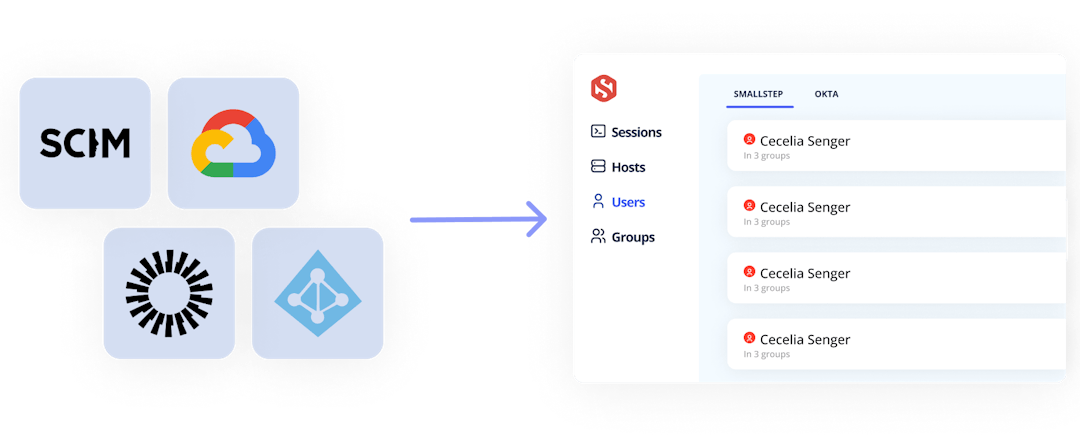
Identity provider user groups are automatically synchronized and used for SSH access control and compliance reporting.

Map host access to users and groups from your identity provider. Revoking a user at the identity provider removes their SSH access instantly.
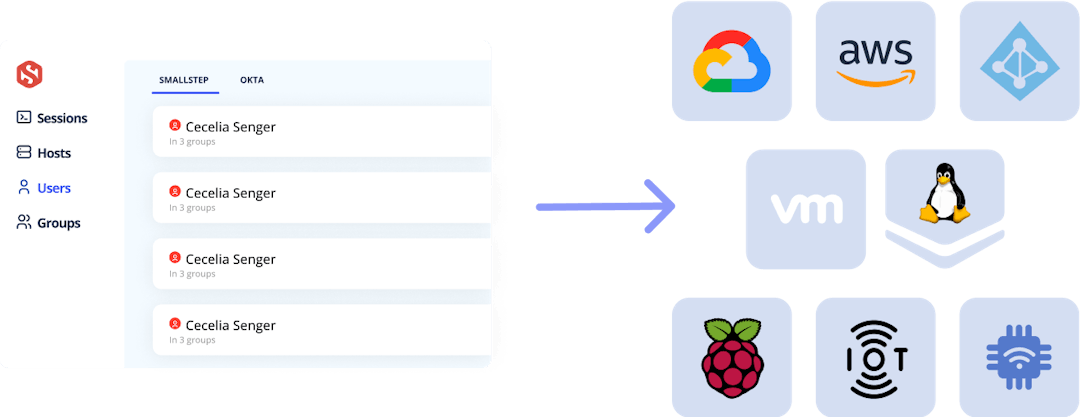
No more adding and removing POSIX users or synchronizing and auditing static public key files across your fleet of hosts.

Reporting and logging of user sessions, access to hosts, and privilege escalations simplify compliance audits.


We were building out new environments, and I didn't want to manage SSH Keys if I could help it.

Remove the barriers preventing you from doing network security right, without sacrificing flexibility and scale.