Everything You Should Know About Wi-Fi Security

Linda Ikechukwu
“In the making of the pie of Wi-Fi security, passwords are only but the crust. Encryption and message integrity are the filling which determines whether the pie stands strong or crumbles under pressure.” ~ ChatGPT
Having a strong and unique Wi-Fi password is good. However, that alone is not enough to keep you safe or guarantee a robust Wi-Fi security.
If you Google “how to improve the security of my Wi-Fi network”, most articles will suggest setting a strong, unique password. However, even if you're using the strongest Wi-Fi password ever known to man — one that is 12 to 16 characters long, with a random mix of uppercase and lowercase letters, numbers, and special characters —, how about the safety of the data transmitted within your network?
Are packets of data transmitted openly over the network? Or, are they encrypted? How strong is the encryption method? And, can anyone on the same network see your internet traffic?
In this article, you will learn about the different elements and grades of Wi-Fi security, how they’re superior to each other, what it means for you, and how you can use that knowledge to stay safe and improve the security of your Wi-Fi network.
The three pillars of Wi-Fi Security
The security of a Wi-Fi network is measured by a combination of three factors:
- The authentication method, which prevents unauthorised access to the network
- The encryption algorithm, which protects wirelessly transmitted data from eavesdropping, ensuring that only the sender and receiver can read it.
- The message integrity algorithm which provides proof against tampering, so authorised messages are not changed over the air by malicious actors.
You've likely encountered terms such as WPA-PSK or WPA2-Enterprise when attempting to connect to or configure a Wi-Fi access-point or router. In Wi-Fi terminology, the "WPA..." denotes the cipher suite of encryption and message integrity algorithms, while the second part specifies the authentication mode available for the Wi-Fi network.
When a client device connects to an access point, several key values are negotiated during the initial handshake to ensure a secure WiFi connection. The specific process used for negotiation and exchange of these key values depends on the algorithm specified by the Wi-Fi security grade (WPA, WPA2, WPA3) or Wi-Fi authentication mode (OPEN, Personal, Enterprise) available to both parties. These key values are then used to facilitate authentication, encryption, and message integrity between the Wi-Fi client and the access point.

Authentication provides access control. The identity of users are verified before granting them access to secure networks, establishing which endpoints or users are and aren't permitted on a Wi-Fi network. For any Wi-Fi network, there are 3 available authentication modes: Open, Personal, Enterprise (more on these later).
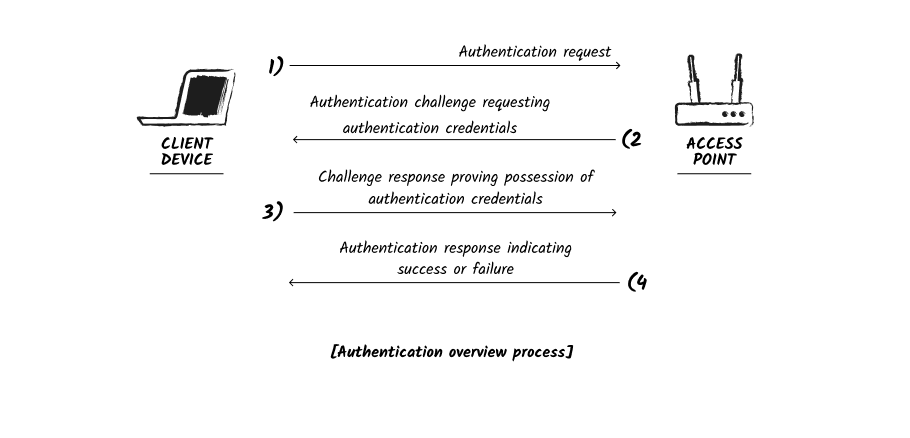
Encryption provides data confidentiality. It prevents unauthorised parties from being able to read the data transmitted between a device and an access point. During the initial handshake, the two communicating parties securely negotiate and exchange a symmetric encryption key, derived by passing the authentication credential and other values into an encryption algorithm. Where there is no authentication credential, there’s usually no network encryption in place.
The encryption key is then used to encrypt and decrypt the data exchanged between both parties, preventing malicious actors connected to the same network from spying on other users' data.

Message integrity, also known as message authentication, ensures or provides proof that data has not been altered in transit. To achieve this, during the initial handshake, before the two parties commence communication, a message authentication algorithm and a secret symmetric message authentication key are securely agreed upon. Before sending a message, the transmitter passes the message data and the secret message authentication key as inputs to the message authentication algorithm.
The result is a Message Integrity Code (MIC) or a Message Authentication Code (MAC), which is then appended to the message being sent before it is encrypted. When the receiver receives the encrypted message, it decrypts the message data, and runs the message data and the secret message authentication key through the previously agreed upon message authentication algorithm. If the MAC calculated by the receiver matches the MAC provided by the transmitter, the data is considered authentic.
The strength of a message integrity process is dependent on the number of bits of the MAC. Therefore, a 128-bit MAC option is more secure than a 64-bit option, which is more secure than a 32-bit option, and so on.

Not all authentication/encryption/message integrity algorithms are not created equally. There are currently four Wi-Fi umbrella security grades: WEP, WPA, WPA2, and WPA3. Each one uses different authentication, encryption, and message integrity protocols to secure WLAN infrastructure and communications, with some being superior to others.
The Wi-Fi network you’re on, could either be open (no authentication and no encryption), have encryption and no authentication, or have encryption and authentication.
Needless to say, the most secure Wi-Fi networks are those with enforced authentication, encryption, and message integrity.
To paint a clearer picture, let’s discuss the different authentication modes in detail.
Relationship between the IEEE and Wi-Fi Alliance
The Institute of Electrical and Electronics Engineers (IEEE) Standards Association is responsible for publishing global standards.
Informed by current scientific advancements and best practices, these standards guide operations across various industries. An example is the IEEE 802.11, which defines guidelines for wireless communication.
Standards benefit manufacturers by providing a technical specification for designs. However, they may not always benefit end users in terms of interoperability. This is because standards can be ambiguous or contain optional features, leading to different interpretations by manufacturers, and ultimately resulting in incompatibility. For instance, will a WLAN product from manufacturer A work with a WLAN product from manufacturer B?
To enforce the interoperability of WLAN products from different manufacturers, the Wi-Fi Alliance was established.
The Wi-Fi Alliance is a non-profit organization formed in 1999, composed of several WLAN hardware manufacturers. They certify WLAN products for interoperability under the "Wi-Fi" trademark. The alliance's rigorous testing program ensures that WLAN products from various manufacturers function together seamlessly.
In other words, if you purchase Wi-Fi certified products, you can connect to other Wi-Fi certified products with the latest security features.
To be Wi-Fi certified, a manufacturer must subject its product to testing against a set of "gold standard" Wi-Fi products. The Wi-Fi Alliance develops its test plan based on the IEEE 802.11 and 802.11i specifications (the document outlining security mechanisms applicable to 802.11 wireless network products). When the standard is ambiguous, the "gold standard" products' behavior determines the correct interpretation, ensuring interoperability.
The Wi-Fi Alliance assigns incremental names to these Wi-Fi security standards based on major updates to the IEEE 802.11 and 802.11i specifications.
For example, if the IEEE updates the 802.11i specification, perhaps by adding a new encryption method, the Wi-Fi Alliance will name that update WPA4. Then, it will require device manufacturers seeking Wi-Fi certification to comply with these updated standards.
WEP, WPA, WPA2, and WPA3 are all approved, interoperable, and standardized implementations of updates and additions to the IEEE 802.11 and 802.11i by the Wi-Fi Alliance.
Wi-Fi Authentication Modes: Open vs. Personal vs Enterprise
As mentioned earlier, Wi-Fi networks can currently be deployed in 3 authentication modes: Open, Personal, Enterprise.
In summary, the choice between Open, Personal, and Enterprise Wi-Fi authentication modes depends on the specific needs for security, ease of use, and network management capabilities.
- Open mode offers deployment convenience at the expense of security,
- Personal mode balances deployment convenience with moderate security,
- While enterprise mode is more complex to deploy, it offers the highest level of security and user management, suitable for environments with sensitive data and the need for strict access control.
| Attribute | OPEN | Personal | Enterprise |
|---|---|---|---|
| Authentication Basis | None; open network without authentication | Pre-shared Key (PSK, a.k.a Wi-Fi password) | Individual User Credentials |
| Key Management | Not applicable | Manual key management; same key for all users | Dynamic key management; unique keys per user |
| Security Protocol | None | WPA/WPA2/WPA3-Personal | WPA/WPA2/WPA3-Enterprise |
| Authentication Method | None; open access | Relies on shared key only | 802.1X authentication using a RADIUS server |
| Use Case | Public Wi-Fi hotspots, Guest networks | Home networks, Small offices | Corporations, Universities, Large organizations |
| User Management | Not applicable | Simplistic; changing PSK affects all users | Granular; can manage users individually |
| Scalability | High; no user management required | Limited scalability due to manual key management | Highly scalable with centralised user management |
Open
An open Wi-Fi network is a wireless network that doesn't require user authentication for access, making it easy for anyone within range to connect — even malicious actors. The wireless client sends an authentication request to the AP, which the AP accepts without question. After authentication, the wireless client associates with the AP, and is granted access. You'll often find this type of network in public spaces like cafes, libraries, airports, and hotels, where providing quick, easy internet access to visitors is a priority.
While there is no authentication on the wireless level, other means of authentication can be implemented to keep away bots. For example, using a captive portal: you can connect to the network without any issues, but as soon as you open your web browser, you see a web page where you have to enter your credentials. Until you enter your credentials, all traffic is blocked.
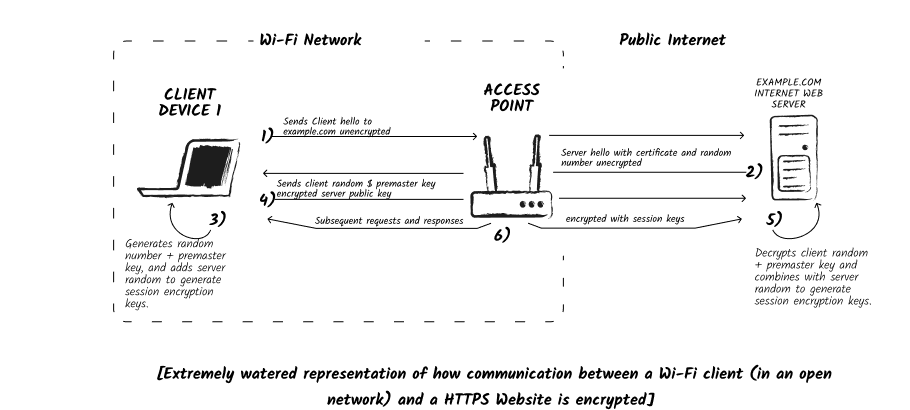
However, since open networks do not require any wireless authentication credentials, they are typically unencrypted. This is because there are no authentication credentials to produce encryption keys with, meaning that malicious actors can likely eavesdrop on traffic exchange.
The access point forwards traffic from client to server or sender to receiver in plain text, without any form of encryption. All DNS queries and HTTP traffic are visible to anyone who connects to the network with a sniffing tool. This is unless the server or receiver has its own encryption mechanism like TLS. As a result, it's recommended to exercise caution when using public open Wi-Fi networks. Avoid inputting sensitive information into forms on websites, unless it's a trusted HTTPS site.
Personal (PSK)
In Personal Wi-Fi networks, every client uses a single shared password to authenticate to the network. Any client wishing to connect to the network must know this password, and the network is safe from unwanted clients and malicious actors as long as the password stays within trusted devices.
This type of Wi-Fi network is perfect for small, controlled environments consisting of a few trustworthy devices, like those at home or in a small office. Beyond a few devices, it becomes limiting and hectic as password updates need to be manually applied to all devices and granular user management is not possible.
Personal Wi-Fi networks offer better security compared to open networks. However, the security is heavily dependent on the level of trust placed in the users. In the event that an individual without proper authorization acquires a shared Wi-Fi password through illicit methods, though unlikely, it is a relatively straightforward process for them to gain access to the network and conduct malicious actions.
For example, if a malicious actor somehow obtains the shared password for a Wi-Fi network, they can set up an imposter Wi-Fi network with the same SSID using a device like Wi-Fi Pineapple. Authorized client devices belonging to the genuine network will auto-connect to any imposter Wi-Fi network with the same SSID and password if they receive a stronger signal from the imposter AP and have chosen to "remember" the network. Once a client device connects to the imposter AP, the malicious actor can view the transmitted traffic, as the shared password is generally used to generate encryption keys.
For such networks, the best practice is to enforce strong passwords and periodically update them to occasionally weed out unwanted access.

Enterprise
Enterprise Wi-Fi authentication mode is ideal for organizations that want strong security, granular access control, and centralized management of credentials and policies. Unlike Personal Wi-Fi authentication mode, where the same password is used for all clients, Enterprise mode uses 802.1X authentication, allowing each client to have their own credentials. As a result, even if one client’s authentication credentials are compromised, the entire network is not endangered.
Each client device in an enterprise network is individually authenticated using an AAA(A) server/system (like a RADIUS server or a DIAMETER). When a client attempts to connect to an access point, the access point transmits the provided credentials to an AAA(A) server/system for verification. The AAA(A) server/system, which serves as a database of authorized users and their corresponding credentials, validates the submitted credentials. If they are legitimate, then it responds with an OK and grants the client device access.
Assigning unique and individual authentication credentials to each device lowers the attack surface area in the event that an authentication credential is compromised, making Enterprise Wi-Fi authentication the most secure Wi-Fi authentication option.
Enterprise Wi-Fi networks support a variety of 802.1X Extensible Authentication Protocol (EAP) authentication types, the most commonly deployed being EAP-TLS, EAP-PEAP, and EAP-TTLS. EAP-TLS is the most secure Enterprise 802.1x authentication option because it uses public key cryptography and certificates instead of static credentials.

The primary reason organizations are hesitant to implement EAP-TLS is the complexity of deployment, which requires the setup of additional infrastructure such as RADIUS servers and a public key infrastructure (PKI) for certificate management in order to manage client and server certificates. All of this can be overwhelming for IT staff without specialized expertise.
Smallstep fixes that. As a comprehensive enterprise network security solution we’ve made it easy for you to roll out 802.1x EAP-TLS Wi-Fi within your infrastructure. Our software includes a RADIUS server, and you can use Jamf, Intune, or any other Mobile Device Management (MDM) platform to issue Wi-Fi client certificates to devices in your infrastructure in minutes.
See our Wi-Fi setup guide for setup instructions for your MDM platform + access point, or Watch our EAP-TLS Wi-Fi setup video on YouTube or Read our deep dive on how certificate-based Wi-Fi authentication works.
Next, let’s look at the encryption side of things.
WEP vs. WPA vs. WPA2 vs. WPA3: The different grades of Wi-Fi security
If you want to be on the most secure Wi-Fi network (think NSA grade), then you should be running WPA3-Enterprise with EAP-TLS.
This section provides an overview of the various grades and version of Wi-Fi security to help you understand why.
| Standard | WEP | WPA | WPA2 | WPA3 |
|---|---|---|---|---|
| Release Year | 1997 | 2003 | 2004 | 2018 |
| Cipher suite | RC4 | TKIP with RC4 | CCMP (AES counter mode encryption, Cipher Block Chaining Message Authentication code (CBC-MAC)) | GCMP (AES counter mode encryption, Galois Message Authentication Mode) & CCMP |
| Supported key size | 64-bit and 128 | 128-bit | 128-bit | 128 and 256 bit |
| Cipher Type | Stream | Stream | Block | Block Cipher (with stream cipher mode) |
| Authentication | Open System & Shared Key | Uses WPA Four-Way-Hanshake to verify possession of correct credentials (PSK or 802.1x) | Uses WPA Four-Way-Hanshake to verify possession of correct credentials (PSK or 802.1x) | Uses Simultaneous Authentication of Equals (SAE) to securely verify possession of correct credentials (PSK or 802.1x) |
Wired Equivalent Privacy (WEP)
Wired Equivalent Privacy (WEP) was the original security standard introduced for wireless network security as part of the flagship IEEE 802.11 specification, with the intention to provide data confidentiality comparable to that of a traditional wired network.
WEP has since been deprecated since 2003. You might still find WEP in use in old embedded devices due to the need for less computational power. We recommend moving away from WEP if possible. Since 2001, there’s been a lot of documented security vulnerabilities.
WEP is flawed in the following ways, to mention a few:
- Repetitive encryption keys: WEP uses the RC4 cipher, where the encryption key is generated by combining a 24-bit Initialization Vector (IV) with a static pre-shared key manually configured on the wireless access point and connecting devices. Despite its intended randomness, the short length of the IV makes it prone to repetition in high-traffic networks, exposing patterns that attackers can analyze to reverse-engineer the static key and decrypt traffic. Sometimes, the IV is even hardcoded into the AP as 802.11 does not specify how IVs are set or changed. And since the IV is tied to the AP, all client and AP pair use the same encryption key.
- Plain text transmission of IV: In WEP encryption, the IV is transmitted plainly from client to device. So, any malicious actor who knows the WEP secret key can decode data packets across the entire network continuously till they tire. There is no provision for backward or forward secrecy.
- Restricted key length scalability: WEP’s usage of a static encryption key + a short IV length of 24 bits to generate the encryption key did not allow for dynamic scaling of the key's complexity with size increase, making it extremely weak against brute force attacks. For example, in a 64-bit WEP implementation, a 24-bit IV allows for about 16 million possible combinations, and the 40-bit static key has just over a trillion possible values. A modern PC can crack both through extensive searching in just a few hours using tools like AirSnort. Even with the introduction of longer 128 and 256-bit WEP implementations, the time required to crack increased linearly, not exponentially, due to the fundamental limitations of the IV and static key approach.
- Flawed Integrity Check: For message integrity, WEP uses the CRC-32 (Cyclic Redundancy Check) algorithm. However, this non-cryptographic checksum is easily manipulated, allowing attackers to alter packets and adjust the checksum without needing the encryption key.
 Source: NullSec
Source: NullSec
WEP supports two authentication methods: Open System authentication and Shared Key authentication. These function a bit differently from the previously discussed OPEN and Personal authentication methods discussed earlier, so let’s discuss them briefly.
WEP Open
A WEP Open System authentication allows for initial connection/ association with the access point without authentication. It's only during data exchange that WEP keys are used to encrypt communications, requiring both the client and the access point to have the same WEP key pre-configured to successfully exchange data.
WEP Shared Key
WEP Shared Key authentication requires the client to have the correct WEP key to be associated with the access point. The access point sends a plain-text challenge to the client, who encrypts and returns it. If the access point decrypts this encrypted response with its WEP key and it matches the original, authentication is granted. Ironically, it's less secure than Open System authentication due to the readable exchange of the plain challenge.
Wireless Protected Access (WPA)
The numerous flaws of WEP necessitated an immediate alternative. However, the slow and meticulous process required to develop a new security specification clashed with the urgency. As a stopgap, the Wi-Fi Alliance released WPA as an interim standard in 2003, while the IEEE developed a more advanced, long-term replacement for WEP.
WPA introduced Personal and Enterprise authentication modes, providing stronger authentication, particularly for enterprise networks.
To facilitate immediate adoption, WPA had to use the same RC4 encryption as the already deployed hardware for WEP. But, it introduced a new scheme for generating encryption keys called Temporal Key Integrity Protocol (TKIP) and the Micheal algorithm for message integrity.
In TKIP, encryption keys are generated from a combination of the authentication credential (PSK or 802.1x), sender’s MAC address, and a TKIP packet sequence number (a 48-bit IV) passed through two different mixing operations. Additionally, using each client’s MAC address as an input to generate encryption keys means that all AP to Client pairs will have different encryption keys (a such improvement from WEP). For message integrity, the message is combined with the shared authentication key and passed through a tagging function to generate a 64-bit Message Integrity Code (MIC).
The use of TKIP and dynamic key generation made WPA significantly more challenging for attackers to compromise the network encryption compared to WEP's static keys. However, WPA was still susceptible to the same RC4 attacks discussed above. Over time, several vulnerabilities in TKIP were discovered, potentially allowing attackers to decrypt packets, inject packets, or conduct replay attacks.
Warning: TKIP has been deprecated since 2012. If your access points still enables TKIP for WPA, you should disable it and upgrade your security protocol.
 Source: Research Gate
Source: Research Gate
Wireless Protected Access 2 (WPA2)
In 2004, the IEEE concluded work on their permanent WEP replacement. The standard was ratified as IEEE 802.11i as an amendment to the original IEEE 802.11 standard for wireless communication.
WPA2 moved away from WEP's RC4 cipher and WPA's TKIP to use the more secure Advanced Encryption Standard (AES) through the Counter Mode Cipher Block Chaining Message Authentication Code Protocol (CCMP). This move to the AES algorithm, widely regarded as one of the most secure symmetric encryption algorithms available, significantly strengthened network security by enhancing encryption and message integrity.
WPA2 uses the four-way handshake mechanism for generating and exchanging encryption keys. Each communication session between an access point and client gets a unique encryption key to protect against the threats of key interception or compromise.
The four-way handshake occurs after a device authenticates with the network. Each side (access point and client) uses inputs like the Pairwise Master Key (PMK), nonces from both the access point and client, and their MAC addresses to independently generate a Pairwise Transient Key (PTK) session encryption key.
After key derivation, both the AP and the client prove to each other that they have derived the same PTK without actually transmitting the PTK itself. They do this by exchanging Message Integrity Codes (MICs) that are calculated using the Key Confirmation Key (KCK), which is part of the PTK.
Beyond improved encryption, WPA2's use of CCMP for message integrity checks is a step forward from TKIP, offering better protection against data tampering and forgery. Its design, free from the backward compatibility constraints to WEP hardware like WPA, allowed for a more secure implementation.
If you're serious about security, WPA2 is the minimum Wi-Fi security standard your network should be running on. It's also currently the most widely deployed Wi-Fi security standard, even in enterprises.
However, despite the fact that WPA2 is a relatively secure Wi-Fi security standard, it would be remiss not to discuss its vulnerabilities, which led to the introduction of WPA3.
The most notable are:
- KRACK (Key Reinstallation Attack): This vulnerability popularised in 2017, allows attackers to exploit decrypt network traffic, hijack connections, and inject content into the traffic stream by forcing nonce reuse. Notably, after the vulnerability was disclosed in 2017, both hardware and software vendors quickly worked to patch their systems to prevent attackers from exploiting the flaw. So, now is a good time to check if your devices have recently been updated with the latest security patches.
- Lack of forward secrecy: In WPA2, the PMK does not change unless the PSK or the authentication credentials are changed. If an attacker manages to capture the PMK and enough traffic, they can potentially decrypt past and future sessions, assuming the PMK remains the same.

WPA2-PPSK
In addition to PSK and Enterprise, WPA2 and WPA3 allow a non-standardized authentication mode called Private Pre-Shared Keys (PPSK), implemented by vendors like Aerohive, Ruckus, Ubiquiti, and Xirrus.
WPA2-PPSK strikes a balance between WPA2-PSK's simplicity and WPA2-Enterprise's robust security. It permits unique passwords for individual devices or a collection of devices within the same personal network, enhancing security by isolating the risk of a single credential compromise to specific devices, rather than the entire network.
However, it's less scalable than WPA2-Enterprise in larger environments, since credential generation and distribution are manual and can be time-consuming as the number of devices increases.
WPA2-PPSK has two flavors: with or without RADIUS.
Without RADIUS, you can have different VLANs, each with its own unique password under one SSID. This version of PPSK is only supported on WPA2 Wi-Fi networks. It is the best option for older or outdated network infrastructure, or highly specialized devices that do not support 802.1x Enterprise authentication, such as game consoles, IoT devices, and washing machines.
With RADIUS, individual devices authorized to access the network can be assigned unique passwords. These passwords are mapped to the respective MAC addresses of the devices in a vendor-provided database within the access point (AP), a controller, or a RADIUS server. When a device attempts to log in, the AP checks the provided passwords against its list of accepted credentials. If a match is found, and the password is associated with that device's MAC address, the device is authenticated and granted access to the network.
The ‘without RADIUS’ flavour of PPSK is supported by WPA2, while the with RADIUS flavor of PPSK is supported by both WPA2 and WPA3 Wi-Fi networks.
Wireless Protected Access 3 (WPA3)
if you’re in a security-sensitive environment and you aren’t running WPA3, you should be migrating to it.
WPA3 was published in 2018 tackle the vulnerabilities found in the WPA2 standard and respond to the changing cyber threat landscape. Since 2020, it has been required for Wi-Fi certification.
WPA3 also introduced some new features to improve authentication, bolster cryptographic strength for sensitive data markets, and protect the resiliency of mission-critical networks.
Some of the most notable features of the WPA3 standard are:
- All-round better security: WPA2-Enterprise only allowed a maximum security level of 128 bits; WPA3-Enterprise allows for 192 bits. WPA3-Enterprise 192-bit mode is the most secure Wi-Fi mode available today, and offers increased security in sensitive domains such as government, defense, and industrial verticals. In addition, WPA3 introduces the 256-bit Galois/Counter Mode (GCM) Protocol and 384-bit Hashed Message Authentication Mode (HMAC) with the Secure Hash Algorithm, which sets a consistent security baseline to better protect sensitive data.
- Efficiency via Parallel Processing: WPA3 uses the Advanced Encryption Standard (AES) in Galois/Counter Mode (GCM), known as GCMP, which is more efficient and secure than WPA2's CCMP. GCMP upgrades Wi-Fi network performance by processing data blocks in parallel. This speeds up the encryption and decryption process, and makes GCMP a better alternative for modern, fast-paced Wi-Fi environments that require high data rates and low latency. Unlike CCMP, which is limited to 128-bit AES, GCMP can employ 128- or 256-bit AES encryption.
- Forward Secrecy and resistance to replay attacks: Unlike WPA2, where encryption keys are derived from a static PSK or authentication credential, GCMP discards the use of the PSK and instead uses a more complex complex interaction that includes ephemeral keys, a commit-exchange phase and a confirmation phase to generate the PMK. This way, if a session key is compromised, past and future communications remain secure, as the static PSK is not used.
- Protection against offline dictionary attacks with SAE: WPA3 addresses the weaknesses of WPA2's four-way handshake by adopting the Simultaneous Authentication of Equals (SAE) handshake. SAE, a more secure and thoroughly tested algorithm, prevents dictionary attacks by generating new encryption keys for each session. SAE, also known as Dragonfly Key Exchange, is grounded in the Diffie-Hellman Key Exchange, which allows two parties to securely exchange a secret key over an insecure channel. Each party generates a temporary pair of public and private keys based on elliptic curve cryptography. They exchange the public keys and combine their private key with the received public key to compute a shared secret. This shared secret then undergoes a series of complex cryptographic transformations to derive the Pairwise Master Key (PMK).
- Enforces management frame protection: Protected Management Frames (PMF), not required in WPA2, are a mandatory feature in WPA3. PMF is crucial for maintaining Wi-Fi connections as these management frames enable important actions like associating with an access point, disassociating, or roaming. PMF safeguards against traffic-based DoS attacks, which exploit forged deauthentication/disassociation management frames to disrupt clients' network connections, forcing them to reauthenticate for a chance to uncover encryption keys or launch an attack like KRACK.
- Imposes server authentication for EAP-TLS Enterprise 802.1x authentication: In WPA2, the client doesn't always check server certificate and might just connect to a duplicate network. By mandating server certificate checks, WPA3 effectively reduces the risk of man-in-the-middle (MitM) attacks and minimizes the risk of credential theft. Users are less likely to input their credentials into a fake network that an attacker could have set up to harvest login information.

💡 For a better detailed overview of how EAP-TLS 802.1x Enterprise Wi-Fi authentication works, read our guide on Certificate-based Wi-Fi Authentication with RADIUS.
WPA3-OWE
OWE stands for Opportunistic Wireless Encryption, also known as Wi-Fi Enhanced Open authentication mode. WPA3-OWE is the open authentication mode introduced by WPA3. It provides data encryption and privacy over an open network, which is an upgrade over typical open networks that lack any security.
Wi-Fi Enhanced Open uses the secure SAE key exchange mechanism to provide each client with a unique session encryption key, which protects data exchange between the client device and the access point. All traffic is encrypted, including management frames.
Migrating from an Open Wi-Fi network to an Enhanced Open Wi-Fi network is possible, as the standard is interoperable and backward compatible. Wi-Fi Enhanced Open can also be deployed in a transition mode which allows for gradual migration without disruption.
With WPA3 OWE, network operators who employ captive portals to regulate network access can improve security while still keeping implementation simple.
Wi-Fi Easy Connect
Another important development that came with WPA3, which you should be aware of, is Wi-Fi Easy Connect.
Wi-Fi Easy Connect was launched as a more secure alternative to WPS, to onboard "headless" IoT devices into the network in a manner that scales for small home networks to large, complex enterprise networks.
Wi-Fi Easy Connect employs the Device Provisioning Protocol (DPP) for device enrolment. DPP uses elliptic curve cryptography for key establishment and the Advanced Encryption Standard (AES) for symmetric encryption. It also introduces a new credential called connectors, which are tied to a physical device and allow IoT devices to be uniquely identified on the network while also applying device-specific access controls and authorization policies to them.
This is an upgrade from what's obtainable with WPS, where IoT devices share the same access credential as every other client device, making it impossible to identify individual devices on a network — a crucial security requirement for IoT networks.
Onboarding a device into a network through Wi-Fi Easy Connect involves the following process:
- There’s a configurator, usually a trusted mobile or network device like a router. And there’s an enrollee, the device being authenticated.
- Every enrollee has a public/private key pair, which the DPP protocol uses to authenticate the device.
- Only a valid configurator can initiate the process of authenticating and provisioning the enrollee into the network by obtaining the enrollee's public key. This measure prevents attackers from hijacking an unprovisioned device.
- A valid configurator can obtain an enrolee’s public key either by scanning a QR code, connecting to a manufacturer cloud database, PHEX, NFC, or Bluetooth.
So, how secure is your Wi-Fi network, and what can you do about it?
If you’ve read up to this point, congratulations!
You now know a great deal about Wi-Fi security: the three pillars of Wi-Fi security, the three different methods of Wi-Fi authentication, the various grades of Wi-Fi encryption, their associated vulnerabilities, and how they are superior (or inferior) to each other.

From everything we’ve covered you now know that the most secure Wi-Fi security grade is WPA3-Enterprise 192 bit mode with EAP-TLS.
If you want to join the S-Tier (most secure gang), watch Apalrd’s video below on how to do so with a UniFi AP + Smallstep.
Interestingly, it’s possible to use WPA3-Enterprise 192-bit mode security in your home network. Check out Carl’s article on rolling out WPA3-Enterprise 192-bit mode security to your home network.
To find out what Wi-Fi security grade your network is running on:
If you don’t administer the Wi-Fi network,
Click the Wi-Fi icon on your device or navigate to Wi-Fi settings to see the Wi-Fi security grade of the network you are connected to. If you see any of the following: WEP, WPA Personal, WPA2 (TKIP), or WPA/WPA2 (TKIP), your best line of action is to disconnect from such network. These security protocols are old, deprecated, insecure, and reduce network reliability and performance.
If you’d rather not disconnect because you need the internet, then consider using a reputable VPN and exercise caution or drawing the attention of the administrator to the security implications.
If you administer the Wi-Fi network,
You’d find what Wi-Fi security grade you’re currently running on from your router admin dashboard page.
Before you do anything else, install the latest firmware updates for your router/access point and other devices to get support for modern Wi-Fi security grades and fixes against known vulnerabilities.
On Personal Networks:
- If your Wi-Fi security grade is currently anything other than: WPA3 Personal, WPA2/WPA3 Transitional, or WPA2 Personal (AES), set Wi-Fi security to WPA3-Personal for the best security. If WPA3-Personal is not supported yet by your devices, check for WPA2/WPA3 Transitional for compatibility with older devices and at the very least WPA2 Personal (AES). WPA2/WPA3 Transitional is a mixed mode that uses WPA3 Personal with devices that support that protocol, while allowing older devices to use WPA2 Personal (AES) instead. Avoid any security setting with TKIP in the name.
- Use a strong Wi-Fi password. To a very large extent, the security of your Personal network comes down to the strength of your password. While picking a password, here are some tips to remember:
- Your password should not be all numbers
- Your password should not include common words, like the name of your car, dog, state, child or your favourite car.
- Instead of coming up with a password that's so hard you won't remember it the next day, the best approach for picking a password is to use 4 random words separated by a dash or period. Go to XKCD.pw, pick 4 random words from different outputs, capitalise the first letter of each word, separate them with a dash or any other special character, and use that as your Wi-Fi password. Such passwords take an exponentially increased amount of time to crack or brute force.
On Enterprise Networks:
- Switch to WPA3-Enterprise (or at the very least WPA2/WPA3 Transitional for older devices) with EAP-TLS. Let Smallstep help you get that deployment done smoothly and in record time 🤷🏽.
- For older devices and infrastructure that may not support the WPA2 or WPA3, move them to a separate SSID or VLAN to to minimize the risk of lateral movement.
- For extra encryption and protection, especially when employees are accessing the network remotely, use a VPN as a second line of defense. With TPM 2.0 and Secure Enclave technology to provide the strongest guarantee that access requests come from specific, verified hardware, Smallstep's Device Identity solution can help you ensure that only company-approved devices can access the VPN.
Want to read more security stuff like this, subscribe our monthly newsletter or join our discord channel.
Linda is a wannabe guitarist, who reads African literature or fiddles with a tennis racket to unwind while navigating the daily grind of helping growth-stage tech startups drive adoption and awareness of their products through tailored content strategies that translate concepts from arcane technical domains into plain and accessible language.



