What is Smallstep?
Certificates are a fundamental part of any non-trivial architecture. They provide the strongest possible way to authenticate users and devices, encrypt communications, protect data integrity, and ensure compliance with security standards.
Smallstep is a comprehensive device identity solution for securely identifying company-owned or company-managed devices using high-assurance cryptographically attested device identity certificates.
As networks and resources become increasingly distributed—with SaaS moving sensitive resources off private networks and BYOD policies introducing personal devices—threats to data confidentiality grow more aggressive. Organizations are seeking more secure methods to ensure that only authorized users on authorized devices can access sensitive resources. Provisioning trusted devices with device-attested client certificates for accessing critical resources within your organisation is the most effective way to achieve this.
Smallstep provides the means to use the strongest possible assurance of device identity to ensure that only trusted company-approved devices can enroll for client certificates to access sensitive organisational resources. This procedure is facilitated through the ACME device attestation enrollment, effectively protecting your organization from data breaches caused by credential compromise or phishing.
With Smallstep, IT/Security/Network Engineers can assign certificates to devices and configure the things that rely on those certificates correctly without needing to know much about PKI.
💡Regardless, if you want to dive deeper into PKI, see some literature from our blog:
Why cryptographic attested device identity?
Many existing solutions provide some flavor of 'device identity' where the device self-reports a unique ID for itself, or the identity is tied to a credential.
But can such device identity be trusted if an independent infallible entity does not attest to it? Does a credential still significantly identify a device if it can be moved between devices? In such scenarios, we make critical assumptions that our devices and services report information is trustworthy.
Claiming device identity should be as substantiated as declaring one's citizenship. Just as one must provide a passport, attested and signed by their nation's government to prove their citizenship, a device should also offer some form of attestation to establish its identity.
Take the SCEP enrollment process ubiquitously employed by MDM platforms.
The Simple Certificate Enrollment Protocol (SCEP) [RFC 8894] simplifies the process of issuing certificates to devices and 'verifying their identity' on a network. The process starts with an employee initiating enrollment through authentication with an MDM agent or link. The employee's device then receives a SCEP payload. This payload contains enrollment instructions, a SCEP server URL, and a challenge password, which the device then uses to obtain a certificate from the organisation's Certificate Authority (CA).
The problem is, in this process, the device does not provide strong evidence about itself when making a request. It's hard to verify that the device belongs to a said organisation or is a known device, because there is no known identity set up for the device the first time it identifies itself. Additionally, SCEP is secured with a password, making it vulnerable to phishing—if a scammer obtains a user's credentials, they could enroll an unauthorised device. Similarly, an attacker who gains access to a configuration profile could use SCEP to obtain a certificate and impersonate the user.
How can controls be implemented to assure that only authorised trusted devices can obtain certificates using your organisation's PKI?
The answer lies in cryptographic attested device identity: a device provides strong signed evidence, backed by hardware-bound keys, independent of the OS or user space, affirming its identity.
Modern devices feature cryptoprocessors (TPMs or Secure Enclaves) that are isolated from the main processor. These cryptoprocessors are shielded from tampering and unauthorized access, even if the primary operating system is compromised. They provide hardware-based security-related functions and perform cryptographic operations. Each cryptoprocessor comes with a unique asymmetric key pair, hard-coded during manufacturing, of which the public part is publicly accessible.
To verify its identity, a device signs a challenge by decrypting data encrypted with its public key. This public key is stored on the organization's device inventory, and the decryption is done using its hardware-bound private key. After successful verification, the device receives an attested device identity certificate. With this certificate, the device can prove its identity to your organisation's Public Key Infrastructure (PKI) and obtain the necessary certificates to access organisational resources. This can be achieved with device attestation and ACME device-attest-01 challenge.
ACME is a client and server protocol that uses "challenges" to ensure a client can prove control over specific identifiers for issuing a certificate. The device-attest-01 challenge allows devices to request attestation from a device inventory. They then forward the signed attestation and Certificate Signing Request (CSR) to a supported ACME server in exchange for a signed certificate from the organisation's PKI.
This process, known as cryptographic device attestation, forms the foundation for secure, automated device enrollment, and is how we protect your resources.
How can you use Smallstep?
The Smallstep Agent is the vehicle through which Smallstep delivers cryptographically attested device identity to your organisation. It is the recommended way to identify devices and get client certificates to devices (Windows, Linux, macOS, ChromeOS) for Enterprise Wi-Fi, VPN, HTTP/3 proxies, or web applications.
It is a lightweight program that runs in the background on devices and manages end-to-end certificate lifecycle for various resources. It works with all TPM 2.0 devices—virtual TPMs, firmware TPMs, or physical TPMs—and on some TEEs and Secure Enclaves (eg. Apple Managed Device Attestation).
To get started, sign up now.
For organisations who do not want to use the agent
If for any reason, you cannot have the Smallstep Agent on your devices, Smallstep can still help you get certificates to devices via your MDM using SCEP. This method is less secure than the cryptographic device attestation offered by the ACME device-attest-01 challenge, which is supported by the Smallstep Agent. Regrettably, major MDM providers have yet to adopt ACME device attestation.
Smallstep integrates with your MDM to deploy client certificates to company-managed devices to enable certificate-based network authentication for Wi-Fi (802.1x EAP-TLS WPA-Enterprise), VPN, ZTNA, etc.
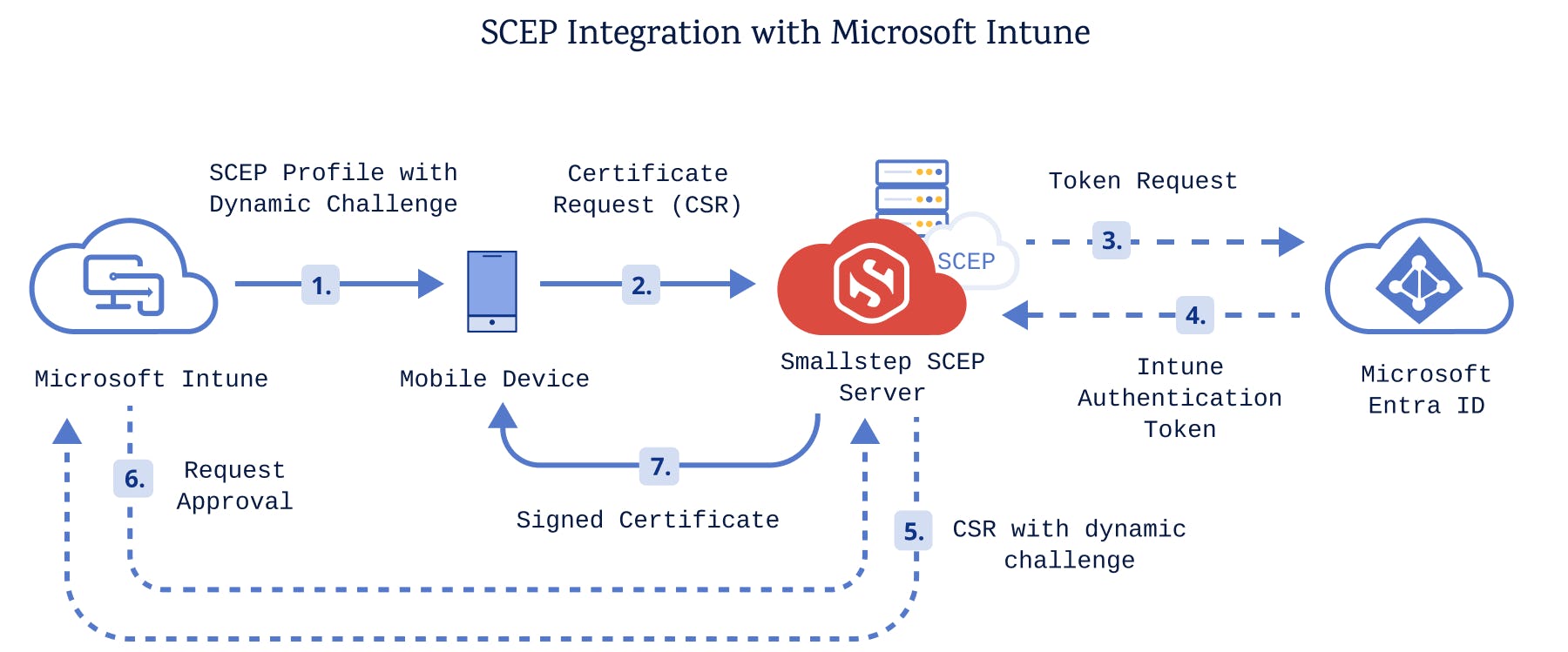
We offer integrations for any MDMs for Apple, Windows, and ChromeOS devices that support Dynamic SCEP like Jamf, Intune, Workspace ONE, Mosyle, Ivanti, and Google Workspace.
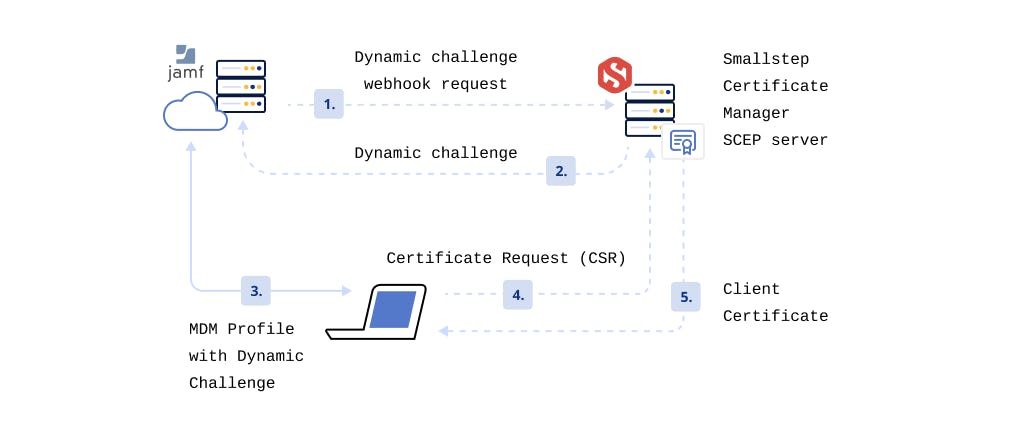
💡 What about MDM’s that do not support Dynamic SCEP?
There are two main approaches to using SCEP as a certificate enrollment protocol: static and dynamic.
In static SCEP, a single challenge password is in every SCEP payload for every device. This practice is insecure and not recommended. Furthermore, it only shows a single user in reporting. We do not support this because we believe it's crucial to provide the most secure options for your infrastructure.
In contrast, for Dynamic SCEP, webhooks are used to generate new challenges and unique passwords for each device, and you would be able to see reporting for all devices.
Smallstep can also be used as a drop-in replacement for Active Directory Certificate Services (ADCS), allowing you to transition from ADCS while still serving legacy workloads. We provide backwards-compatible support for SCEP and NDES, and also let you bring your existing Root CA with you, so you can get up and running in minutes.
The Smallstep ecosystem
Depending on what’s best for your infrastructure and current reality, Smallstep offers different deployment options to meets your needs:
Smallstep SaaS cloud offering
The Smallstep Saas cloud offering is our default recommended offering, unless you have security requirements that prohibit you from using a cloud CA. We also provide an API, Terraform Provider, and Ansible Collection for automation and IaC integration.
Smallstep Run Anywhere
The Smallstep Run Anywhere is a copy of our hosted SaaS software that can be deployed in any customer-managed data center or cloud hosting provider. This solution allows customers to manage their own infrastructure and meet compliance while still being able to use Smallstep’s tech stack to issue and manage certificates.
At its core, Run Anywhere requires a Kubernetes cluster for compute resources. It plugs into a PostgreSQL database, Redis instance, load balancing solution, and either a KMS or HSM. If you would like to deploy Run Anywhere into a GCP, AWS, or Azure environment, we have Terraform modules available for use or reference. Alternatively, users may work with Smallstep to configure their own solutions for other cloud hosting providers and data centers as desired.
Talk to Smallstep’s Customer Engineering Team at support.smallstep.com to design a deployment custom-tailored to all of your security needs.
Smallstep open-source toolchain
Our open source toolchain is the most popular open-source certificate management toolchain, and was designed for DevOps and homelab or POC use cases. However, it’s not a device identity platform, and doesn’t solve the problems listed above out-of-the-box.
Our open-source toolchain provides IT/Security/DevOps engineers with an extensive internal PKI toolchain, which includes everything needed to automate the deployment and management (renewal, revocation, and monitoring) of certificates for a broad range of contexts, use cases, and environments.
We offer robust integration solutions for securing network connections to various resources like servers, databases, internal web applications, Kubernetes clusters, GitHub Actions, VPNs, VMs, Wi-Fi, managed devices, and more. With Smallstep, your PKI can serve as a unified foundation for cryptographic encryption and authentication for all your devices, people, and workloads.
Our open-source toolchain for certificate and PKI management features 3 components:
- step CLI: A user-friendly command-line interface to build, operate, and automate PKI systems, with built-in support for ACME & the
device-attest-01challenge. - step-ca: A powerful online CA for secure, automated certificate management.
- step-issuer and autocert: Kubernetes-native solutions for seamless certificate issuance and management in containerized environments.
Join our open-source Discord community.
Step CA pro
Step CA Pro is Smallstep's drop-in upgrade for our open-source Certificate Authority server, offering advanced features, support, and compliance options. It extends our open source with high availability, active revocation, FIPS compliance, simpler integrations and APIs, and device identity features.
Step CA Pro is ideal for organisations who want full On-Prem Control or need to make the transition from open-source to commercial to access Device Identity capabilities and advanced compliance options.
With Step CA Pro, just like our open source packages, you maintain full control over the CA and signing keys while benefiting from our cloud-based integrations and management interface.
Interested? Reach out to our Sales team.
Last updated on February 3, 2026
Introducing
Device Identity
Ensure that only company-owned devices can access your enterprise's most sensitive resources.